LeetCode – Coin Change Problem | Dynamic Programming | JavaScript
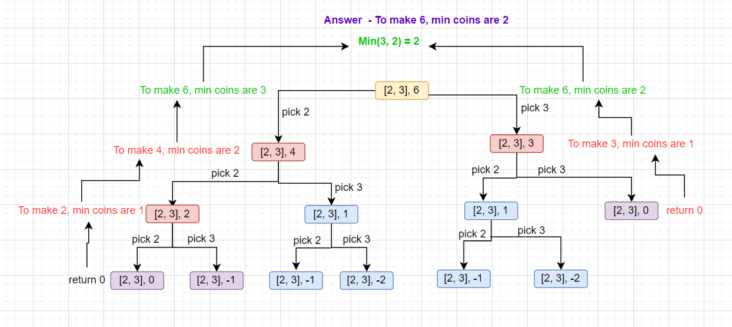
LeetCode – Coin Change Problem Problem LeetCode Link – https://leetcode.com/problems/coin-change/ You are given an integer array coins representing coins of different denominations and an integer amount representing a total amount of money. Return the fewest number of coins that you need to make up that amount. If that amount of money cannot be made up by any combination of the […]
Read More →